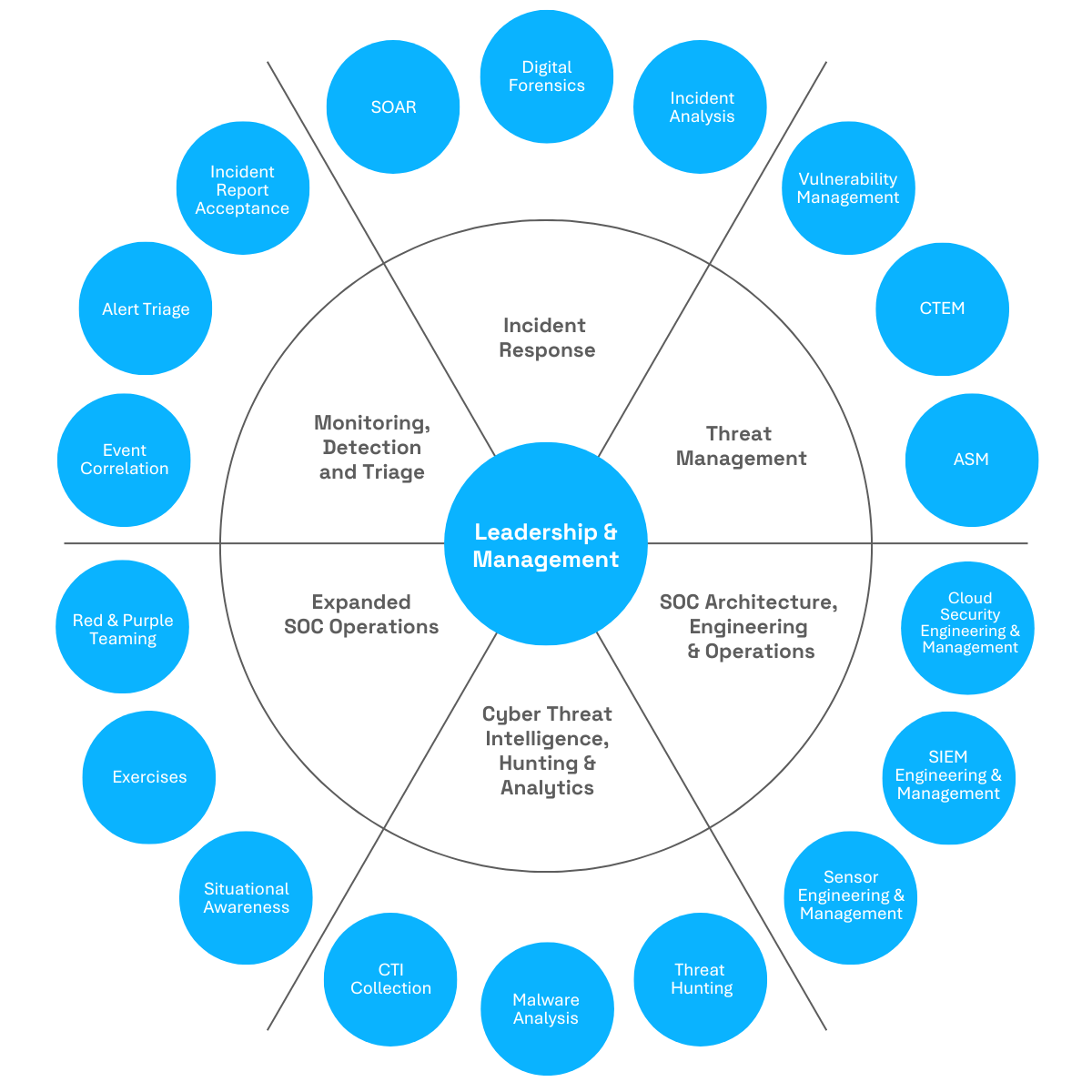
-
Attacks remain undetected for weeks, causing major financial and reputational damage.
-
Inefficient processes delay response, leading to higher costs and downtime.
-
Poor visibility results in wasted investments in tools or personnel.
-
Compliance objectives are at risk – potentially triggering fines or lost contracts.